In December we told you how we are trying to make technology work for government. To discover how best to solve our common issues, the technical team have been working with our colleagues across government and suppliers.
One issue consistently raised was email security. We’ve tackled this together to find not only a solution, but one with strong benefits as well.
The people we’ve worked with
Government has some really big data owners like HMRC and DWP. We also have experts in security like CESG, and a broad range of scale and technical capability in central and local government.
Initially we talked to as many people as possible to find out what they did, what they needed, and what would work for them. We also talked to experts in industry, including email service providers, and specialists in email security and trust.
Some of these people joined our discovery and provided valuable information and insight. For example most government organisations operate two parallel email services with complex configurations routing via the PSN and the internet which means it can be difficult for organisations to trace their full email security stack.
The main requirements of a new design were:
-
is what I send secure in transit?
-
is it properly protected when it gets there?
-
how will I know the two needs above have been met?
In addition organisations adopt change at different speeds. The ones that move first need to know they won’t be left out in the cold and asked:
What we discovered
Departments need to work together securely. Having a secure network such as the Public Services Network (PSN) allows them to share and publish services without having to worry too much about protection from the wider world. The network even includes commercial organisations providing services to government.
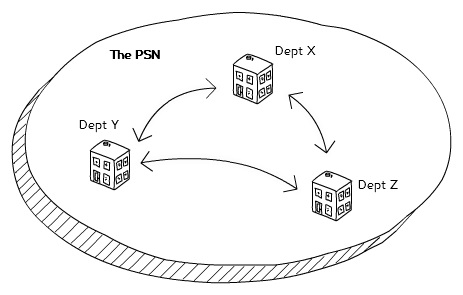
Three organisations exchange information inside the PSN.Creative commons attribution. Nick Woodcraft.
But the nature of technology in government is changing. Email is very much a commodity service. It's well established and understood, and the technology used is fairly homogeneous and mature. Every organisation uses it, and all in much the same way.
And, like other common applications, email has moved to the cloud, bringing with it the benefits of reduced cost, improved reliability, and continuous improvement.
While the new security classifications have allowed a lot to change in the last year, many organisations are still catching up. Government is keen to move to cloud-based email services. Some departments already have, but security is still a big concern, and we can no longer depend just on the network for protection.
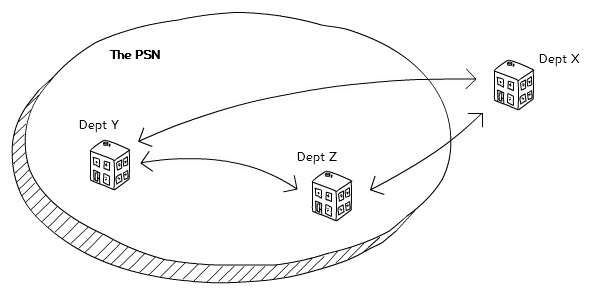
Two organisations inside the PSN exchange information with an organisation outside the PSN.Creative Commons Attribution. Nick Woodcraft.
What we did
Our research told us we needed three things:
- encryption
- verification
- assurance
To meet these needs we’re using open encryption and verification protocols and a combination of a monitoring tool and existing assurance.
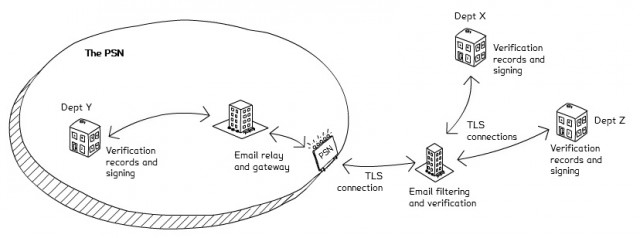
Organisations inside the PSN exchange emails with organisations outside the PSN using TLS encryption and DMARC verification. Creative commons attribution. Nick Woodcraft.
Encryption
Several encryption standards exist, but only Transport Layer Security (TLS) has the high adoption and low burden on the end user needed. TLS protects email in transit between email services, and we are telling government organisations to use policy to ensure it is used in any email exchanges over the internet including, as far as possible, when talking to people outside government.
Our HMRC colleagues highlighted the need for clear guidance on implementing TLS to make sure it provides the proper security. This has been answered by CESG who maintain a list of preferred cryptographic profiles and have recently published guidance on TLS to support its use in government.
Verification
Preventing spoofed or phishing emails is key for providing greater confidence that an email is genuine. HMRC are leaders in this area, and have published a white paper on combating email fraud. They are supporting our approach to provide verification by Domain-based Message Authentication, Reporting and Conformance (DMARC).
DMARC uses a combination of open standards like DomainKeys Identified Mail (DKIM) and Sender Policy Framework (SPF), and reporting to help an organisation understand how it’s email domains are being used or misused. It also allows you to set a policy telling other organisations how to treat email that does not appear to come from you.
DMARC is widely implemented in banking and online services, and the National Crime Agency is working with industry to use it for fraud prevention. We hope that by using it in government we will encourage its adoption country-wide.
Assurance
When you send or receive an email you don’t get any indication of how it was sent, and the people looking after the servers get limited information. Although TLS and DMARC are widely supported open protocols, the nature of the Simple Mail Transfer Protocol (SMTP) on which email is built makes it difficult to get assurance about their implementation.
To provide this we are building a tool to monitor TLS and DMARC use across government, providing a way to check if a service is secure. It will give you a dashboard of the domains in your organisation, a way to check whether an email sent between two domains should be secure, and a whitelist of domains that are setup securely.
The tool is already in alpha and going through user testing. We’re making it available to a limited number of people this week to help iron out any issues before going live. Contact CTS if you’d like to be involved. Once we’re happy it works as intended we’ll make it available to everyone in government and open source the code so it can be reused and developed elsewhere.
The Output
By collaborating across government we’re not only setting a standard for what email security should look like, but one that is interoperable and easy to use.
We’ve published a detailed guide that explains more about what government organisations need to do to securely send and receive email over the internet. It also provides guidance on legacy domains, such as gsi.gov.uk and gcsx.gov.uk. We’re also updating the email gateways and filtering on the PSN to ensure the standards we’re setting are supported inside and outside the network.
Making the changes needed will vary by organisation - common cloud-based email services have all the options available out of the box - but where organisations need help we’ll work out the best way to provide it, through documentation and advice.
The goal is for all government organisations to meet this standard and implement it as soon as is practical. We’ll use the assurance tool to monitor implementation and see what other activity we might need to support this change.
The benefits
The benefits of using the secure email standard are clear. Government organisations can continue to work together securely, but will also have assurance that they can safely exchange email with people outside of government too - without needing to connect to a special network or do any government-special configuration to do it.
But it goes further than that with reduced costs, increased flexibility, and access to better tools for end users.
You’ll be able to follow our work on this blog and GDS main blog. Departments and agencies interested in collaborating with CTS can contact us viacontact.cts@digital.cabinet-office.gov.uk